Tailored Adversary Emulation
To stay one step ahead
In the cyber world, government agencies, private companies, and critical infrastructure entities are deeply interconnected. An attack on one impacts multiple others.
We take on the perspective of cyber adversaries to assess the vulnerability and risk associated with your networks and environments, so you can better prevent, respond to, and understand cyber incidents.
Mission-Tailored Risk Assessments
Adversaries attack certain organizations for certain reasons. Those reasons inform the tactics, techniques, and procedures (TTPs) they use to access and exfiltrate or manipulate the data.
Our high-value asset (HVA) assessments help to identify and map your systems with sensitive data that could cause significant mission, operational, or personal loss — or compromise citizen services — if accessed by a malicious actor. Risk and vulnerability assessments identify relevant threats to your organization as well as structural flaws and weaknesses. We map adversary TTPs to the MITRE ATT&CK® framework to ensure a comprehensive assessment of strategies they might use to access or disrupt a specific customer’s mission and environment.
We provide tailored insights on prioritized threats and risks from the adversary community. Our data-driven risk assessments identify the adversaries who would target your specific environment, how they might do it, and which use cases they may apply to access various data types.
Run The TRAPs (Tailored Risk Assessment Packages)
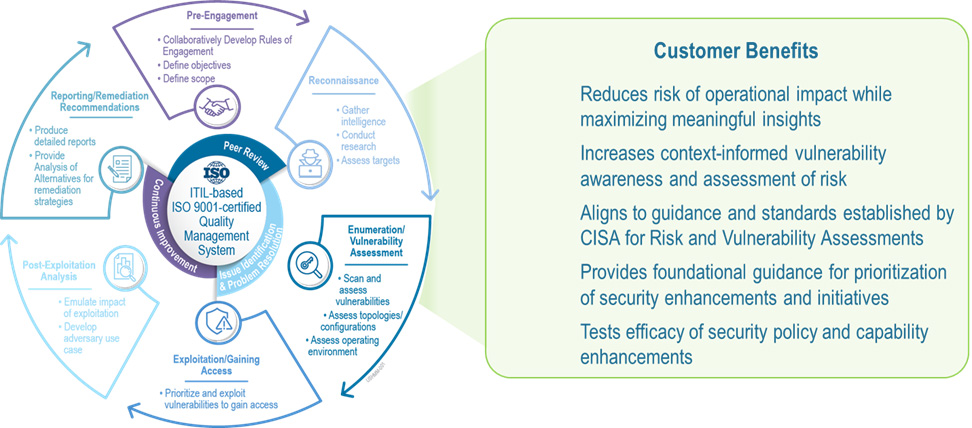
Evolving CISA and other Federal guidance is pushing organizations to increase the frequency of penetration testing, to get a better handle on their risk profile.
Supporting this best practice, ShorePoint provides Red/Blue/Purple Team support to test your security. Using the same TTPs an attacker may use, the exercises help identify weaknesses, inform priorities, and support compliance.
Our penetration testing capabilities are delivered through white box/black box/gray box driven assessments based on organizational Rules of Engagement tailored to provide granular insights into the security risks of the organization and/or specific systems.
Expert Guidance, From Diverse Customer Experiences
Cyber bad actors don’t just attack Federal systems. And they don’t just target IT systems. They look for vulnerabilities across all organization types, probing for openings in IT networks, the Internet of Things (IoT), and operational technology (OT) systems.
ShorePoint has worked with a broad and diverse set of government and private sector companies — large, distributed enterprises, and smaller organizations. Our guidance is enriched by the diversity of our customers’ missions, informing strategies and best practices to minimize your risks and make your organization more resilient.
Only ShorePoint
ShorePoint has worked with a range of Federal, state, local, tribal, and territorial (SLTT) government entities and across the majority of the 16 critical infrastructure sectors to assess risk in the high-value target environments throughout our nation. We know how to tailor services for your mission and environment.
Adversary Emulation & Penetration Testing Capabilities
- Adversary Emulation
- Application Security Testing Program Development and Delivery
- Red Teaming
- Blue Teaming
- Purple Teaming
- White/Gray/Black Box Testing
- Breach Investigations
- IT/OT/IoT Assessments
- High-Value Asset (HVA) Assessments
- Penetration Testing
- Risk and Vulnerability Assessments
- Security Architecture Reviews





