ShorePoint offers an innovative modified Zero Trust Architecture (ZTA) Framework to guide our Agile ZTA Implementation Methodology in our customers’ environments. This framework is differentiated by our establishment of Data Identification and Data Classification as the critical foundation to guide strategies and priorities across the pillars in context of zero trust.
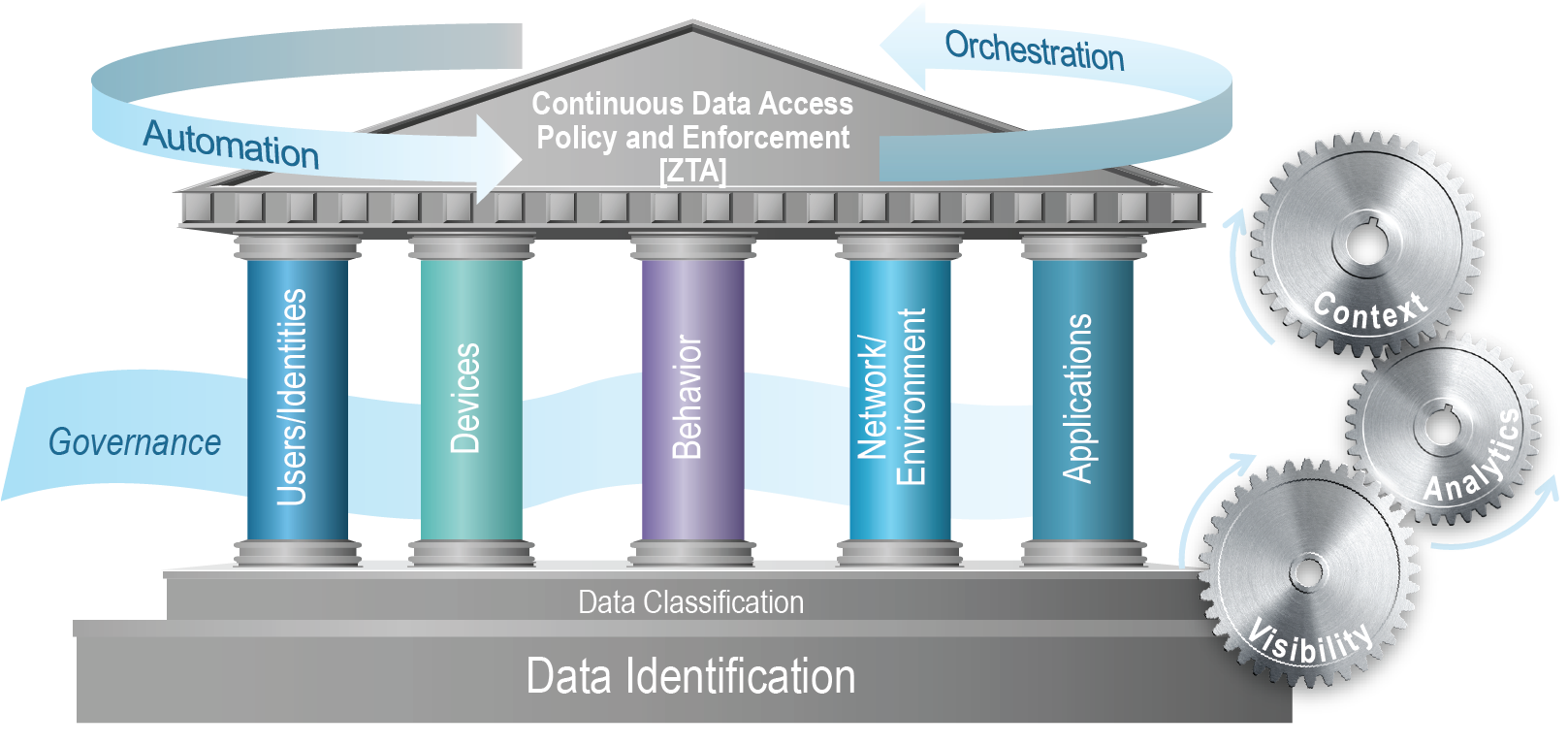
Reinforced by OMB in its Zero Trust Strategy Memorandum M-22-09, our ZTA Framework retains the considerations for governance, automation and orchestration, and visibility/analytics that must be considered across the framework and within each pillar. The automation of a dynamically updated and enforced trust algorithm within a highly mature ZTA requires integrated context across these pillars tied to rules and policies that determine authorization levels for specific data assets within the enterprise.
Built on our ZTA Framework, ShorePoint’s Agile ZTA Implementation Methodology identifies and prioritizes zero trust capabilities for implementation by assessing both expansion of ZTA across systems and expansion of capabilities within pillars tied to each system.
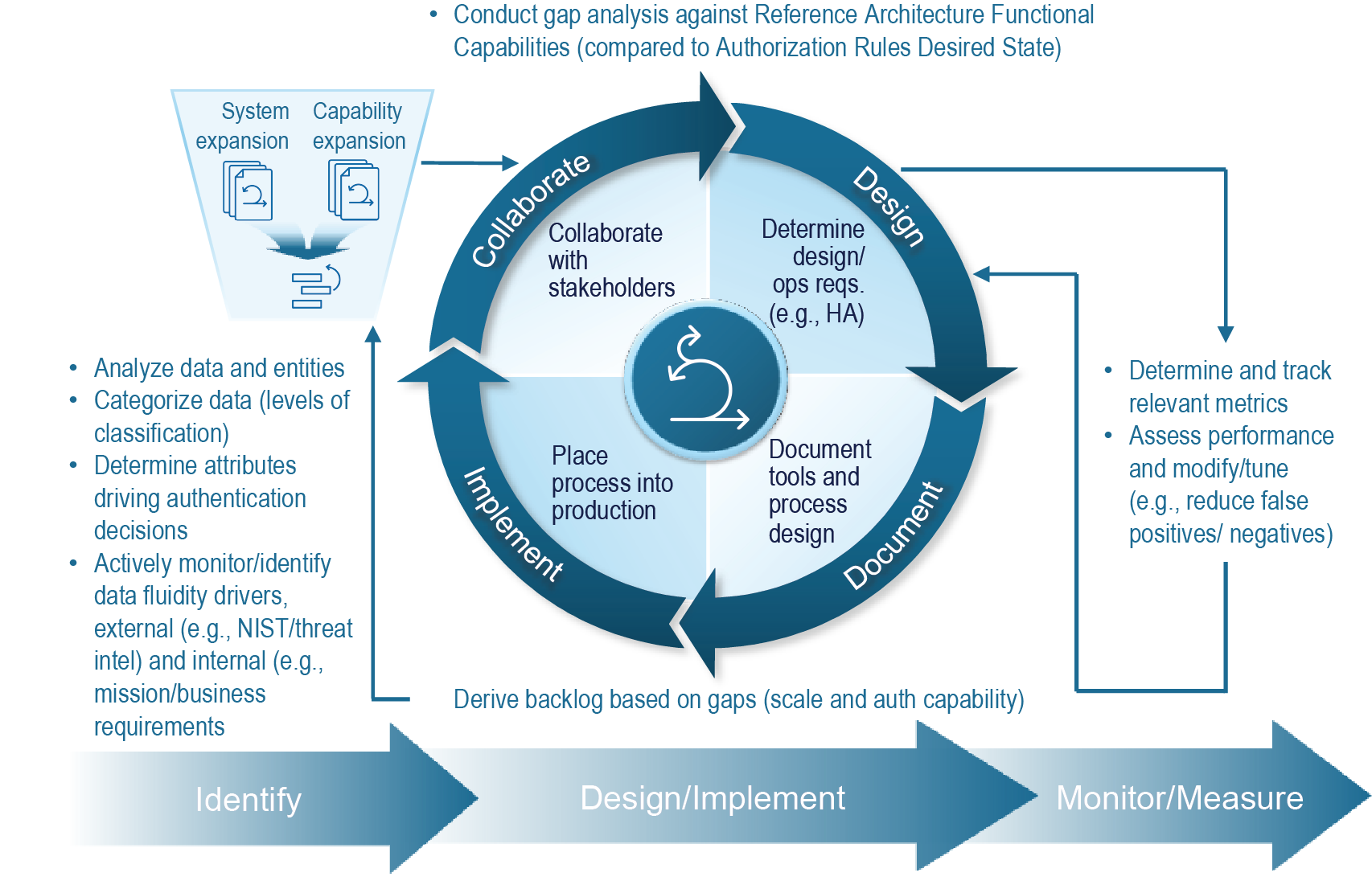
Through our ZTA Framework and Agile Implementation Methodology, ShorePoint helps stakeholders:
- understand the importance of having data drive the strategy
- prioritize appropriate systems and applications for migration to ZTA
- consider authorization requirements across pillars for systems and applications in context of the data that resides within them
Our high-performing, mission-enabling ZTA Framework and Agile Implementation Methodology is keeping our customers ahead of the Zero Trust implementation curve. Through smart integrations that maximize existing cyber investments and informed guidance on solutions that can scale to meet mission needs, ShorePoint delivers a functional and adaptable ZTA tailored to your agency’s environment.
Contact us today for a demonstration on how our innovative frameworks and methodologies can help you align to industry best practices and guidance to meet your cybersecurity modernization goals.




